Manually re-enroll a Hybrid Azure AD Join Windows 10 / Windows 11 device to Microsoft Intune without loosing the current configuration
Edit 01/06/2022 : updating this article to include Azure Virtual Desktop Windows 10 / Windows 11 multi-session enrollment command using Device Credential
——–
There are several ways to enroll a Windows 10 PC to Microsoft Intune:
Manually
- During the Out-of-the-box Experience (OOBE), when starting a Windows 10 PC for the first time
- In the Windows Settings, after the PC configuration
Manual enrollment will require that the user enters his Azure AD credentials.
Automatically
- Using Azure AD Join + automatic Intune enrollment
- Using Hybrid Azure AD Join + automatic Intune enrollment
Automatic enrollment can be triggered using a Group Policy, SCCM Co-Management or Windows AutoPilot.
Windows 10 automatic enrollment requires the creation of public DNS records enterpriseregistration and enterpriseenrollment. More info here.
However, sometimes it is possible that a Windows 10 PC is in an inconsistent enrollment state, with error “The sync could not be initiated“.
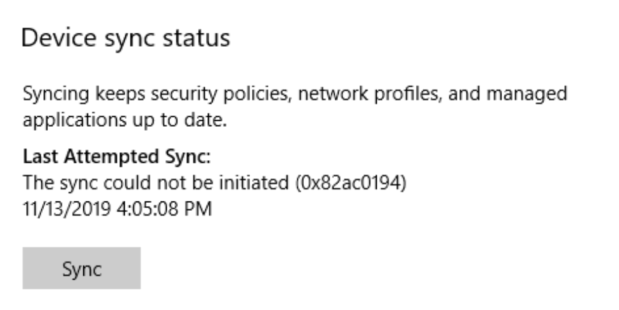
This can happen because:
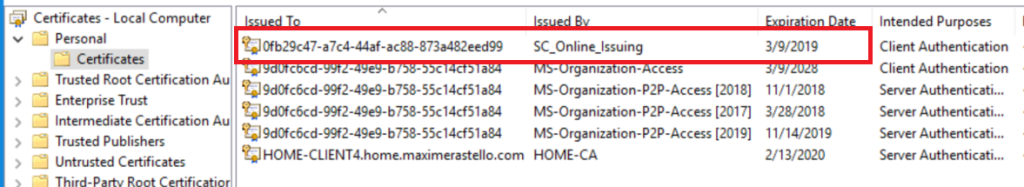
- The PC was shut down during a long time, and the Microsoft Intune certificate is expired (located in Local Machine / Certificates / Personal)
- Someone manually deleted the Microsoft Intune certificate
- The PC is enrolled in another Intune tenant
Prerequisites: check Hybrid Azure AD Join status
Before re-enrolling your device to Microsoft Intune, you need to make sure that the certificates for Hybrid Azure AD Join are not expired as well.
Follow this procedure to Manually re-register a Windows 10 / Windows 11 or Windows Server machine in Hybrid Azure AD Join.
Method 1: With data and configuration loss
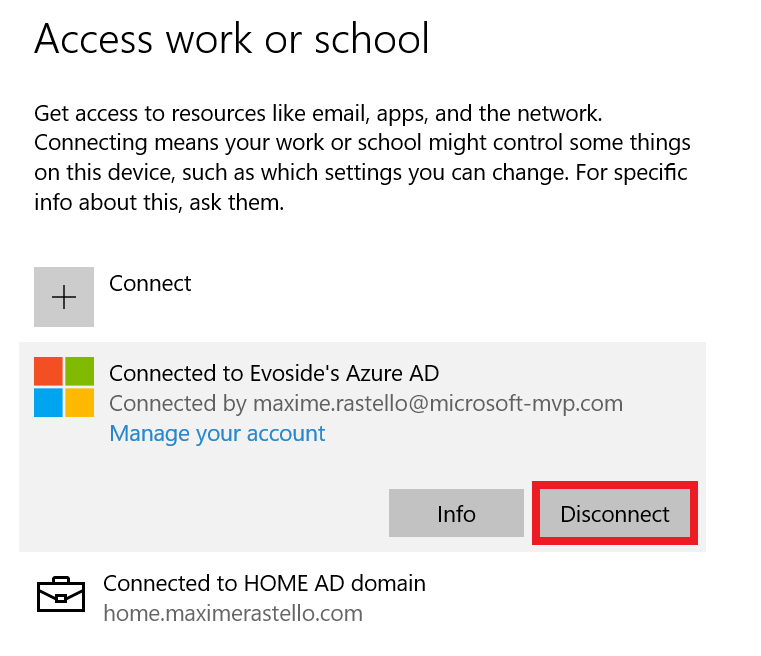
The easiest way to unenroll a Windows 10 PC from Microsoft Intune is to disconnect the work or school account.
Just go to All settings > Accounts > Access work or school, select your corporate account and click Disconnect.
Important: this menu is not available on Windows 10 / Windows 11 multi-session edition for Azure Virtual Desktop.
However, the problem with this is that all data and configuration pushed by Microsoft Intune will be deleted from the PC.
Method 2: Without data or configuration loss
There is a way to manually re-enroll your Windows 10 PC without loosing all the current configuration and apps deployed by Microsoft Intune.
This method is not officially supported by Microsoft
As you may know, automatic enrollment can be triggered either by a Group Policy Object or by the SCCM client on a co-managed device.
In both cases, the feature will basically create a scheduled task to enroll the PC at next logon. The command is different if you are trying to enroll Windows 10 / Windows 11 Enterprise multi-session devices from Azure Virtual Desktop (using Device Credential) or a regular Windows 10 / Windows 11 device using User Credential:
Windows 10 / Windows 11 Enterprise (with User Credential)
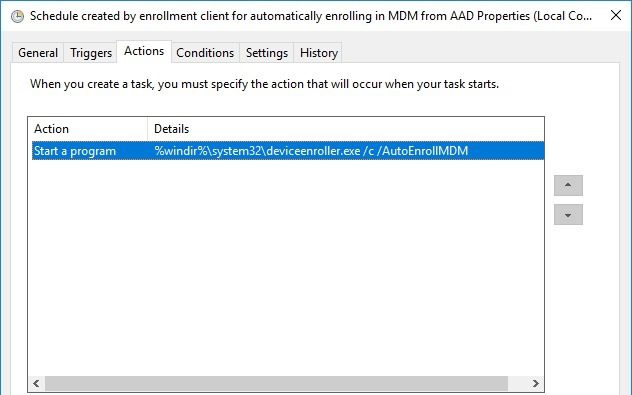
Task launched in the SYSTEM context:
%windir%\system32\deviceenroller.exe /c /AutoEnrollMDM
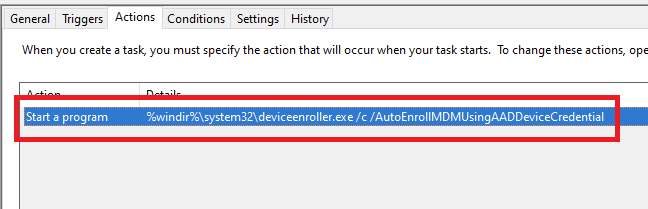
Windows 10 / Windows 11 Enterprise Multi-session for Azure Virtual Desktop (with Device Credential)
Task launched in the SYSTEM context:
%windir%\system32\deviceenroller.exe /c /AutoEnrollMDMUsingAADDeviceCredentialTo manually re-enroll the PC, we will need to clean up the environment and relaunch this command in the SYSTEM context to re-enroll the PC.
Here are the steps that you need to follow to make it work:
- Delete stale scheduled tasks
- Delete stale registry keys
- Delete the Intune enrollment certificate
- Restart the enrollment process
Step 1: Delete stale scheduled tasks
Follow this procedure:
- Run the Task Scheduler as an administrator.
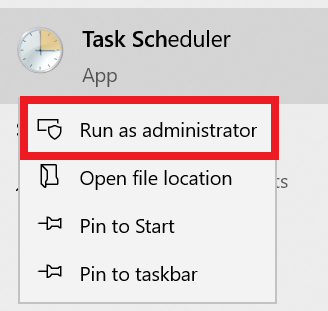
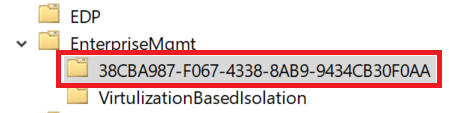
- Go to Task Scheduler Library > Microsoft > Windows > EnterpriseMgmt. Write down the enrollment ID somewhere, you will need it for the cleanup.
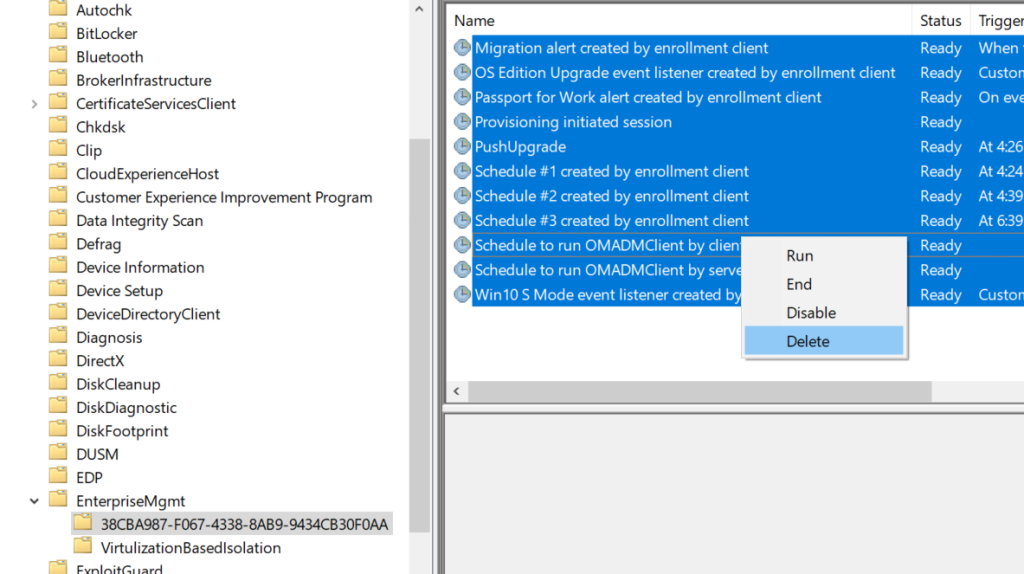
- Delete all the existing tasks the enrollment folder.
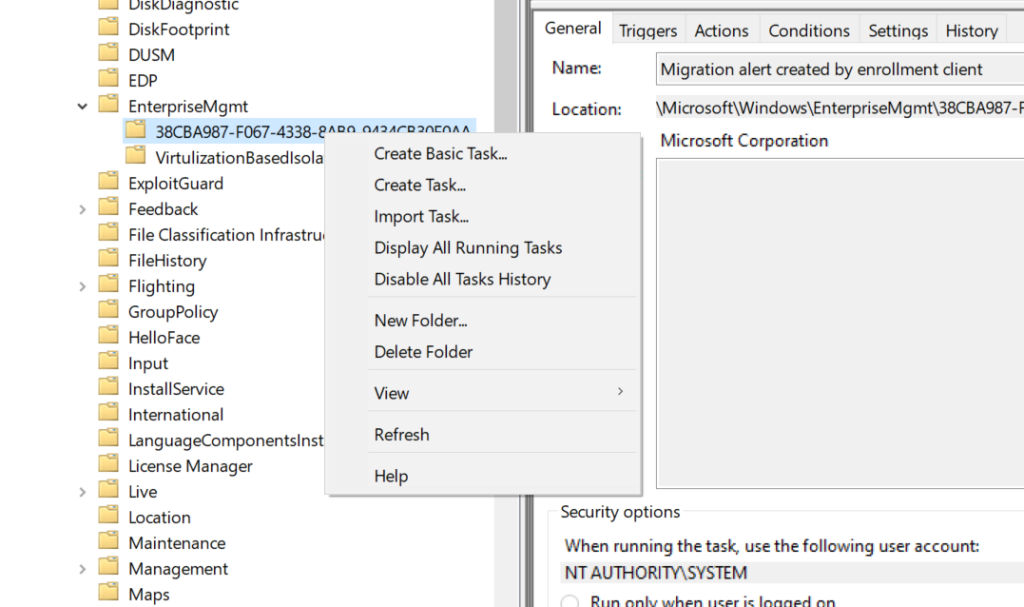
- Delete the enrollment ID folder.
Step 2: delete stale registry keys
Use the previous enrollment ID to search the regitry:
- Open the Registry Editor as an administrator.
- Search for the enrollment ID you wrote in the following locations and if found, delete the key that is containing the ID:
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Enrollments\xxxxxxxxxxxxx
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Enrollments\Status\xxxxxxxxxxxxx
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\EnterpriseResourceManager\Tracked\xxxxxxxxxxxxx
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\PolicyManager\AdmxInstalled\xxxxxxxxxxxxx
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\PolicyManager\Providers\xxxxxxxxxxxxx
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Provisioning\OMADM\Accounts\xxxxxxxxxxxxx
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Provisioning\OMADM\Logger\xxxxxxxxxxxxx
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Provisioning\OMADM\Sessions\xxxxxxxxxxxxx
DO NOT delete registry keys that are not in the list above. They will be overwritten after the new enrollment.
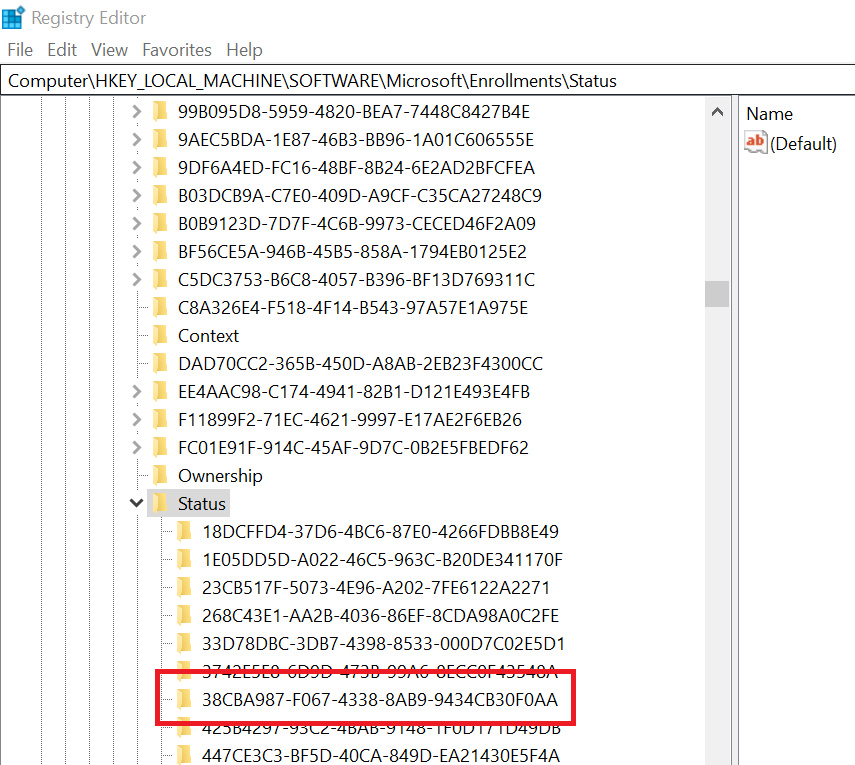
Step 3: delete the Intune enrollment certificate
Follow the procedure:
- Search for the option “Manage computer certificates” or use the command certlm.msc as an administrator.
- Go to Personal > Certificates and delete the certificate issued by either “Microsoft Intune MDM Device CA” or “SC_Online_Issuing” (depending on the date of the enrollment).

Step 4: Restart the enrollment process
To be properly executed, the enrollment command must be entered in a SYSTEM context. We will use the PSExec tool for that purpose.
- Download the PSExec tool from Microsoft website
- Use PSExec to launch a Command Prompt as SYSTEM:
psexec /i /s cmd- In the Command Prompt, enter one of the following command depending on your enrollment type:
Windows 10 / Windows 11 Enterprise (using User Credential)
%windir%\system32\deviceenroller.exe /c /AutoEnrollMDMWindows 10 / Windows 11 Enterprise Multisession for Azure Virtual Desktop (using User Credential)
%windir%\system32\deviceenroller.exe /c /AutoEnrollMDMUsingAADDeviceCredential- In the computer certificate store, check that a new Intune certificate has been enrolled for the device:
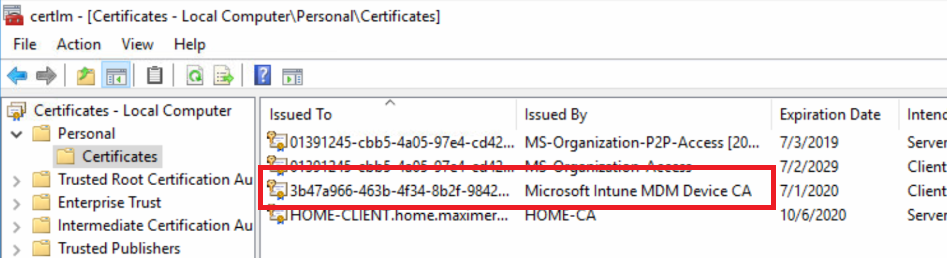
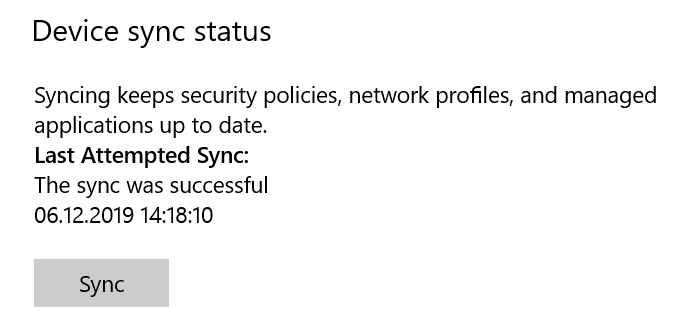
- You are now ready to start a policy sync from the Windows Settings, and check that the connection with the Intune service is now OK:



Thank you very much! Manual enrollment finally fixed my issue.
hi,
in an Hybrid join with SCCM device. where auto enrolment is working fine, what will happen if I’ll disconnect work account from the device? will it than re-enroll it automatically as it did for the first time?
Hello,
Deleting a work or school account will not Disjoin device in Hybrid Azure AD, as HAAD is a device enrollment and not a user enrollment.
Great work, appreciate your effort. Saved a lot of time and struggle.
Great work and great info!
Thank you
“Hello,
Deleting a work or school account will not Disjoin device in Hybrid Azure AD, as HAAD is a device enrollment and not a user enrollment.”
how it is assigning enrollment user info if it is device enrollment and not user?
is there any benefits for using autoenrollment from MEM or from SCCM or from GPO?
Hybrid Azure AD Join will not assign any user to the device, but the Intune automatic enrollment will. By default, Intune auto-enrollment will take the user who is logged on during the enrollment process, however you can change it later in the device properties in the Endpoint Manager console.
Thanks!! This helped a lot!
Even as Admin I was not able to delete the Enrollment ID folder
Make sure you deleted all the tasks in the folder before deleting it
Thank you Maxime, this worked like a charm!
Hi. Thanks for this post, really useful for me while moving PC’s between two AD’s and two Intune tenants, it saved me having to re-install the PCs. I was able to just rip everything out, move the device to the new AD and tenant and re-enroll.
For anyone that finds it useful I created it as a PowerShell script you find here:
https://github.com/steve-prentice/powershell-scripts/blob/master/Remove-IntuneCurrentEnrollment.ps1
Hi, if I run the %windir%\system32\deviceenroller.exe /c /AutoEnrollMDM
I don’t see a new MDM certificate in the personal certificate store, any ideas?
Kind regards,
Steven
Thanks Maxime for this great info.
Help us a lot in our troubleshooting.
Keep going doing good atricles.
All the best!
I had a notebook (hybrid joined) with MDM “none” and owner “none” in Azure. Hours of searching and here in “Method 2” I found the solution. The device is now correctly assigned to the user again in the MDM. I couldn’t delete the Enrollment ID folder either, although it was empty. But that’s just a cosmetic issue. Many Thanks.
Hopefully you will still read this. We have done the above and it works great devices are now appearing in intune, but what we have noticed is that the apps assigned to the device just goes into a stale “waiting for install status” and this does not change have tried a few things did a leave re-join for azure side and have even deleted the Azure AD record and let it re-sync from AD Connect, did not make any difference. Have restarted the intune management service ran syncs from device, or intune still same even unassigned re-assigned different users compliance policies and device configurations works fine it is only the application side of things not working, did you perhaps experience this issue please?
You can always delete the appid thats associated with your app in the registry and run a portal sync. The app should attempt an install shortly after that.
Thank you Maxime, this was really helpful and worked perfectly well and resolved my issue!
Amazing information, thank you! I wish I could have found this sooner. In case it helps the find this, these are some of the errors I ran into when failing to bulk enroll to azure ad and intune.
———–
“Your device is already being managed by an organization”
The device is already enrolled. You can contact your system administrator with the error code 8018000a
AAD Cloud AP plugin call GenericCallPkg returned error: 0xC0048512
The get join response operation callback failed with exit code: Unknown HResult Error code: 0x801c0058
This works great to resolve some of my AVD multi-session hosts dropping from Intune. However, the description in Method 2 Step 4 for Windows 10 / Windows 11 Enterprise Multisession for Azure Virtual Desktop (using User Credential) should be for “(using Device Credential)”.
Thanks for the help in fixing this issue!
Hello, thanks for your effort. You are the best
Thank you so much. I have spent hours searching for a solution. And now I have one.
Would something like this work on an AD joined + AAD registered device? Not quite hybrid, but almost there 🙂
Thank you so much. I’ve been struggling all week trying to correctly enroll my devices. This has been such a lifesaver.
Thanks for this valuable contribution!
I was able to get a stale device back in Intune
Kiki Biancatti ssw.com.au
Thank you very mucho. My workers are stupid. I have to do everything myself and podać im na dacy solution
Thank you very much for this. I have spent hours troubleshooting a single PC and this worked.
Still works like a charm!
I’ve automated it with Powershell:
Function Start-IntuneWorkorSchoolAccountSync {
[void][Windows.Management.MdmSessionManager,Windows.Management,ContentType=WindowsRuntime]
$session = [Windows.Management.MdmSessionManager]::TryCreateSession()
[void]$session.StartAsync()
Write-Output “Sync Initiated!”
}
Function Start-IntuneEnrollment {
#Reference:
#https://www.maximerastello.com/manually-re-enroll-a-co-managed-or-hybrid-azure-ad-join-windows-10-pc-to-microsoft-intune-without-loosing-current-configuration
[CmdletBinding()]
param (
[Parameter()]
[string]$LogFile
)
# Start logging if LogFile is specified
if ($LogFile)
{
Try { Start-Transcript -Append $LogFile }
Catch { Write-Error $_.Exception.Message }
}
# Get All Task Relating to EnterpriseEnrollment:
$ScheduledTask = Get-ScheduledTask -TaskName “Schedule to run OMADMClient by client”
# Get All the EnrolmentID’s
$MDMEnrollmentIDs = @((($ScheduledTask).taskpath).Trim(‘\Microsoft\Windows\EnterpriseMgmt\’))
# Removing ScheduledTasks Relating to EnterpriseEnrollment:
Get-ScheduledTask -TaskPath $ScheduledTask.TaskPath | ForEach-Object {
Write-Verbose “Removing: $($_.TaskPath)$($_.TaskName)”
Unregister-ScheduledTask -TaskPath $_.TaskPath -TaskName $_.TaskName -Confirm:$false
}
# Remove MDM Enrollment Related Registry Entries and Files:
$MDMEnrollmentREGPaths = @(
‘HKLM:\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tree\Microsoft\Windows\EnterpriseMgmt’,
‘HKLM:\SOFTWARE\Microsoft\Enrollments’,
‘HKLM:\SOFTWARE\Microsoft\Enrollments\Status\’,
‘HKLM:\SOFTWARE\Microsoft\EnterpriseResourceManager\Tracked’,
‘HKLM:\SOFTWARE\Microsoft\PolicyManager\AdmxInstalled’,
‘HKLM:\SOFTWARE\Microsoft\PolicyManager\Providers’,
‘HKLM:\SOFTWARE\Microsoft\Provisioning\OMADM\Accounts’,
‘HKLM:\SOFTWARE\Microsoft\Provisioning\OMADM\Logger’,
‘HKLM:\SOFTWARE\Microsoft\Provisioning\OMADM\Sessions’
)
# Remove Files, Folders and Tasks:
Foreach ($MDMEnrollmentID in $MDMEnrollmentIDs)
{
$MDMEnrollmentIDPath = “$env:windir\System32\Tasks\Microsoft\Windows\EnterpriseMgmt\$MDMEnrollmentID”
If (Test-Path $MDMEnrollmentIDPath)
{
Try
{
Write-Verbose “Removing: $MDMEnrollmentIDPath ”
Remove-Item -Path $MDMEnrollmentIDPath -Recurse -ErrorAction SilentlyContinue
Foreach ($Path in $MDMEnrollmentREGPaths)
{
Write-Verbose “Removing: $Path\$MDMEnrollmentID”
Remove-Item -Path “$path\$MDMEnrollmentID” -Force -Recurse -ErrorAction SilentlyContinue
}
}
Catch
{
Write-Warning $_.Exception.Message
}
}
}
# Remove old certificates:
Get-ChildItem Cert:\LocalMachine\My | Where-Object { $_.Issuer -match ‘CN=Microsoft Intune MDM Device CA’ } | Remove-Item -Force
# Start AutoEnrollment and sync:
Write-Verbose “Starting AutoEnrollment.”
Start-Process -FilePath “$env:windir\System32\deviceenroller.exe” -ArgumentList “/c /AutoEnrollMDM” -Wait
Write-Verbose “Sleeping 30 Seconds.”
Start-Sleep 30
Start-IntuneWorkorSchoolAccountSync
Write-Verbose “Sleeping 60 Seconds.”
Start-Sleep 60
# Create a registry key:
New-Item -Path “HKLM:\SOFTWARE\Microsoft\Enrollments\” -Name “IntuneCleanupMDMEnrollmentsRunOnce” -ItemType String -Value “True” | Out-Null
Write-Output “Please Check if the Device is Visible in Intune.”
# Stop logging:
if ($LogFile) { Stop-Transcript }
}
Start-IntuneEnrollment -Verbose
Device was working as co managed but something went wrong and now it is getting managed from SCCM
It will be great help , if this issue will be fixed
Thank you for this!!!!!
Thank you so much for this tutorial, it worked just as expected!
Great article. Thanks much!
Hi, Thank you so much, but I used %windir%\system32\deviceenroller.exe /c /AutoEnrollMDM. I don’t see a new MDM certificate in the personal certificate store; any ideas?
Here is a script that worked for me:
Function Start-IntuneWorkorSchoolAccountSync {
[void][Windows.Management.MdmSessionManager,Windows.Management,ContentType=WindowsRuntime]
$session = [Windows.Management.MdmSessionManager]::TryCreateSession()
[void]$session.StartAsync()
Write-Output “Sync Initiated!”
}
Function Start-IntuneEnrollment {
[CmdletBinding()]
param (
[Parameter()]
[string]$LogFile
)
# Start logging if LogFile is specified
if ($LogFile) {
Try { Start-Transcript -Append $LogFile }
Catch { Write-Error $_.Exception.Message }
}
# Get All Task Relating to EnterpriseEnrollment:
$ScheduledTask = Get-ScheduledTask -TaskName “Schedule created by dm client for dual enrollment to Mmpc” -ErrorAction SilentlyContinue
if ($null -eq $ScheduledTask) {
Write-Warning “Scheduled task ‘Schedule to run OMADMClient by client’ not found.”
} else {
# Get All the EnrolmentID’s
$MDMEnrollmentIDs = @((($ScheduledTask).taskpath).Trim(‘\Microsoft\Windows\EnterpriseMgmt\’))
# Removing ScheduledTasks Relating to EnterpriseEnrollment:
Get-ScheduledTask -TaskPath $ScheduledTask.TaskPath | ForEach-Object {
Write-Verbose “Removing: $($_.TaskPath)$($_.TaskName)”
Unregister-ScheduledTask -TaskPath $_.TaskPath -TaskName $_.TaskName -Confirm:$false
}
# Remove MDM Enrollment Related Registry Entries and Files:
$MDMEnrollmentREGPaths = @(
‘HKLM:\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tree\Microsoft\Windows\EnterpriseMgmt’,
‘HKLM:\SOFTWARE\Microsoft\Enrollments’,
‘HKLM:\SOFTWARE\Microsoft\Enrollments\Status\’,
‘HKLM:\SOFTWARE\Microsoft\EnterpriseResourceManager\Tracked’,
‘HKLM:\SOFTWARE\Microsoft\PolicyManager\AdmxInstalled’,
‘HKLM:\SOFTWARE\Microsoft\PolicyManager\Providers’,
‘HKLM:\SOFTWARE\Microsoft\Provisioning\OMADM\Accounts’,
‘HKLM:\SOFTWARE\Microsoft\Provisioning\OMADM\Logger’,
‘HKLM:\SOFTWARE\Microsoft\Provisioning\OMADM\Sessions’
)
# Remove Files, Folders and Tasks:
Foreach ($MDMEnrollmentID in $MDMEnrollmentIDs) {
$MDMEnrollmentIDPath = “$env:windir\System32\Tasks\Microsoft\Windows\EnterpriseMgmt\$MDMEnrollmentID”
If (Test-Path $MDMEnrollmentIDPath) {
Try {
Write-Verbose “Removing: $MDMEnrollmentIDPath”
Remove-Item -Path $MDMEnrollmentIDPath -Recurse -ErrorAction SilentlyContinue
Foreach ($Path in $MDMEnrollmentREGPaths) {
Write-Verbose “Removing: $Path\$MDMEnrollmentID”
Remove-Item -Path “$path\$MDMEnrollmentID” -Force -Recurse -ErrorAction SilentlyContinue
}
}
Catch {
Write-Warning $_.Exception.Message
}
}
}
}
# Remove old certificates:
Write-Verbose “Removing old certificates.”
Get-ChildItem Cert:\LocalMachine\My | Where-Object { $_.Issuer -match ‘CN=Microsoft Intune MDM Device CA’ } | Remove-Item -Force
# Start AutoEnrollment and sync:
Write-Verbose “Starting AutoEnrollment (Deviceenroller -AutoEnrollMDM).”
Start-Process -FilePath “$env:windir\System32\deviceenroller.exe” -ArgumentList “/c /AutoEnrollMDM” -Wait
Write-Verbose “Sleeping 30 Seconds.”
Start-Sleep 30
Write-Verbose “Starting IntuneWorkorSchoolAccountSync.”
Start-IntuneWorkorSchoolAccountSync
Write-Verbose “Sleeping 60 Seconds.”
Start-Sleep 60
# Create a registry key:
New-Item -Path “HKLM:\SOFTWARE\Microsoft\Enrollments\” -Name “IntuneCleanupMDMEnrollmentsRunOnce” -ItemType String -Value “True” | Out-Null
Write-Output “Completed.”
# Stop logging:
if ($LogFile) { Stop-Transcript }
}
Start-IntuneEnrollment -Verbose