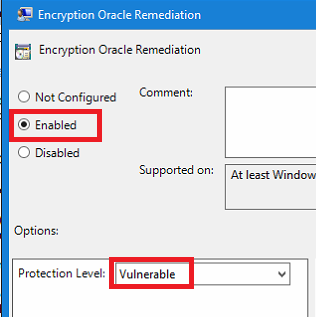
Use Azure AD Cloud Kerberos ticket for on-premises resources
Microsoft has released for a long time now the ability for Azure Active Directory (now Microsoft Entra ID) to deliver a cloud Kerberos ticket when a user opens its Windows session.
Cloud Kerberos trust has been used by several Microsoft products in the past few years:
- Windows Hello for Business Cloud Kerberos Trust
- FIDO2 security key authentication for on-premises resources
- Azure AD Authentication to Azure PaaS services from on-premises machines
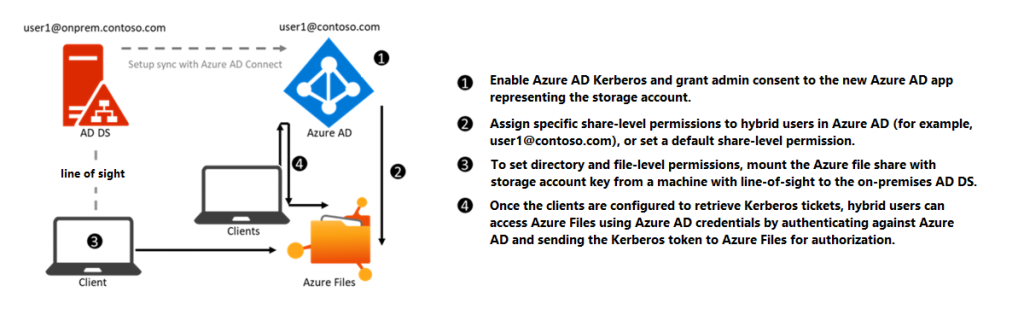
This diagram shows how a device authenticates to a cloud storage account using Azure AD Kerberos authentication:
Scenarios
I’ve been able to test the following scenarios:
- Authenticate to a Kerberos-based web application hosted on a domain-joined IIS server (doc here)
- Authenticate to Exchange Server web services (OWA, ECP, Autodiscover, EWS…) when Kerberos authentication is enabled with ASA Credential (doc here)
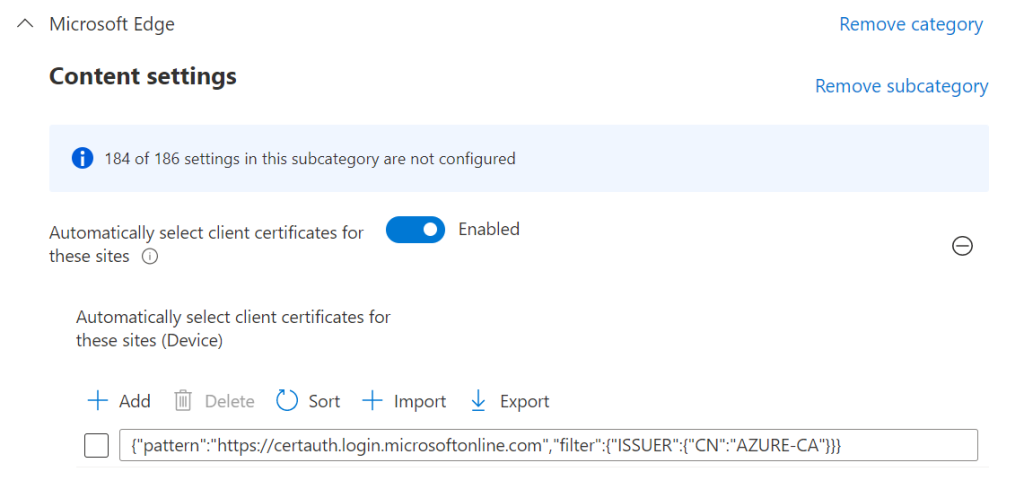
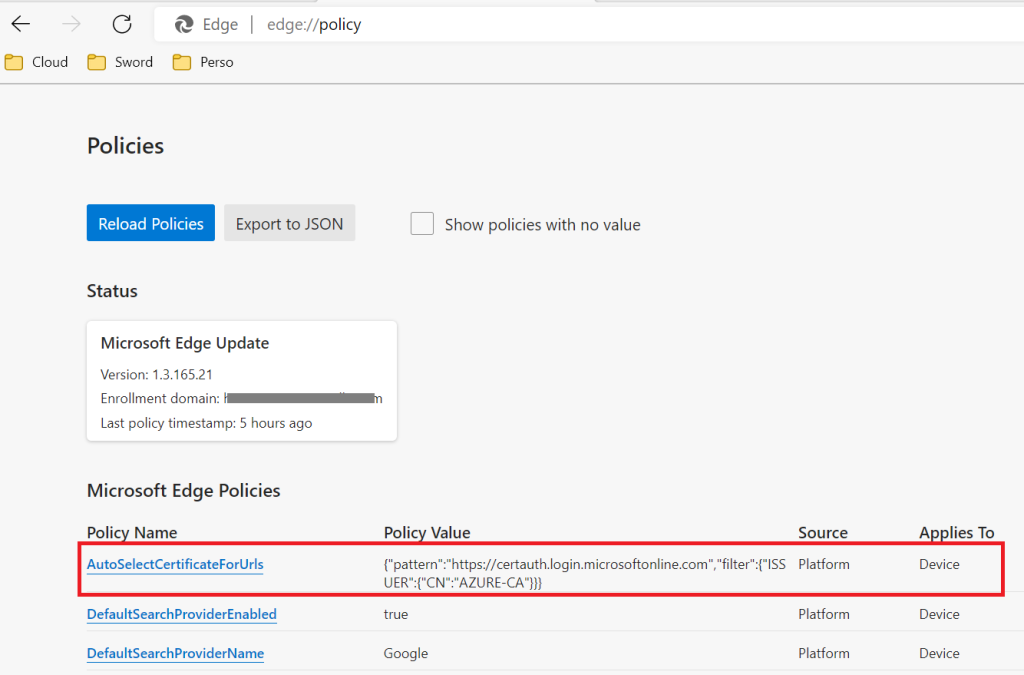
Using an Azure AD Kerberos ticket instead of an Active Directory Kerberos ticket could be useful in the following situations:
- You have access to a Kerberos-based web application but your device is not in a light of sight of a domain controller
- You published a Kerberos-based web application using Microsoft Entra Global Secure Access but the client cannot connect to a domain controller through the tunnel
Note: only TCP is currently supported by the Microsoft Entra Global Secure Access client at the moment.
Prerequisites
To be able to leverage Azure AD Kerberos authentication, the following prerequisites must be met:
- Your web application is configured to use Active Directory Kerberos Authentication
- The device used for app access must be Hybrid Azure AD Joined or Azure AD Joined
- Users must be synced from AD to Azure AD
- Azure AD Kerberos Trust must be configured using the Azure AD Hybrid Authentication Management PowerShell module (doc here)
- Cloud Kerberos retrieval must be activated at user logon on the device by one of the following methods:
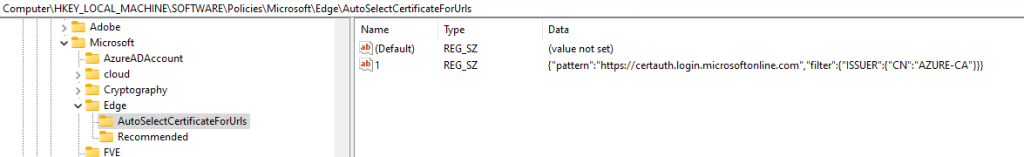
CSP : Kerberos/CloudKerberosTicketRetrievalEnabled set to 1
GPO : Administrative Templates\System\Kerberos\Allow retrieving the Azure AD Kerberos Ticket Granting Ticket during logon
Registry : reg add HKLM\SYSTEM\CurrentControlSet\Control\Lsa\Kerberos\Parameters /v CloudKerberosTicketRetrievalEnabled /t REG_DWORD /d 1
How it works
When Azure AD Kerberos Trust is properly configured, a Cloud Kerberos ticket is generated for the user when you first log on to a Windows or Windows Server machine.
You can see the Kerberos tickets currently available by using the klist command:
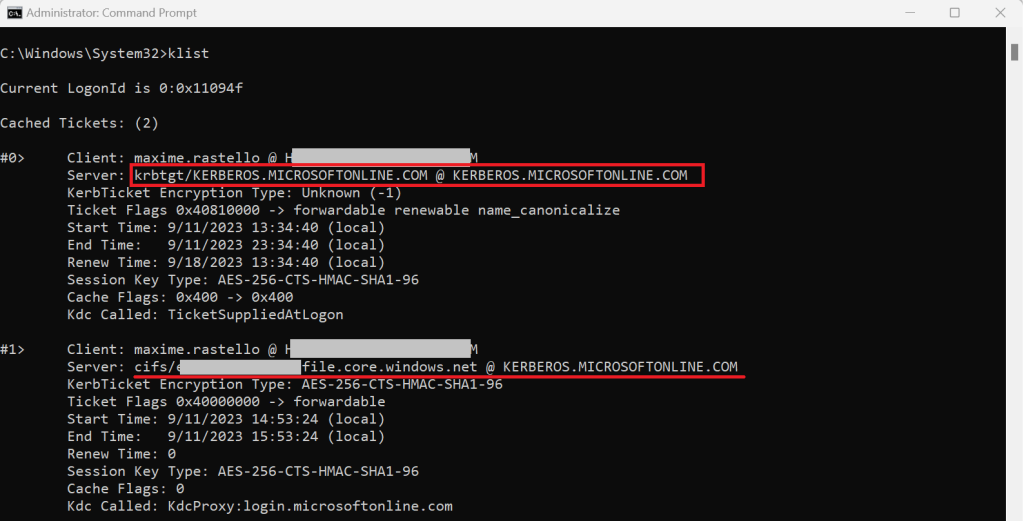
The principle is simple: we will configure your Windows workstation to map a Kerberos web app authentication with this Cloud Kerberos ticket using the cloud realm KERBEROS.MICROSOFTONLINE.COM
Kerberos realm configuration
To map the Cloud Kerberos ticket with your on-premises web apps, we will use the setting Hostname to Kerberos realm mappings. You can configure this setting using:
- A Microsoft Intune Settings catalog profile
- A Group Policy Object (GPO)
- A command line
Using GPO
- Create a new GPO and link it to your workstations
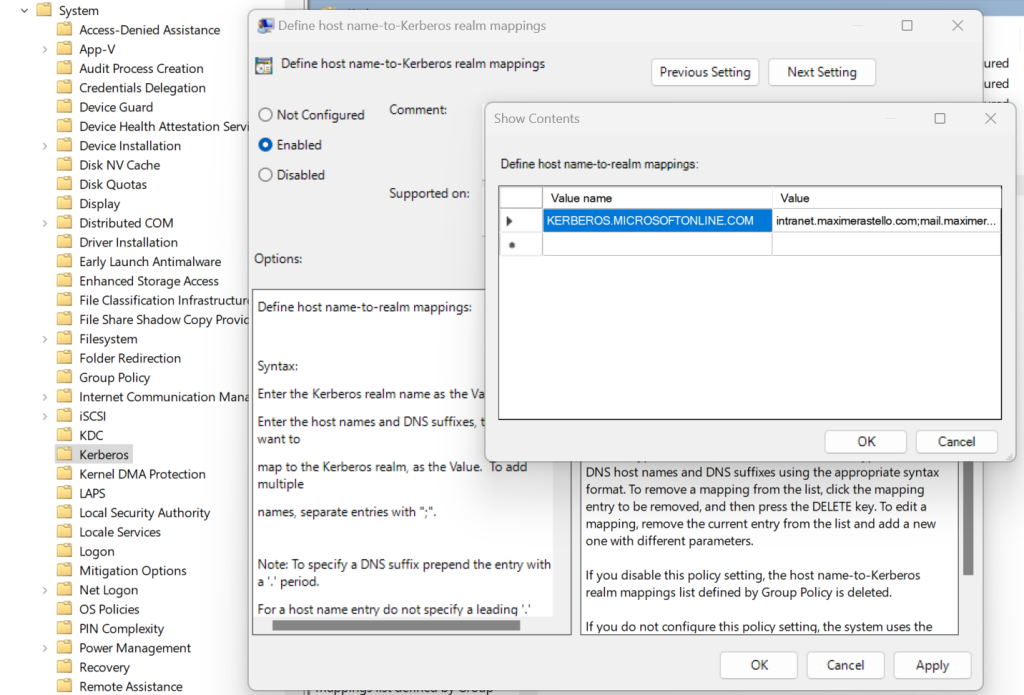
- Go to Computer Configuration > Administrative Templates > System > Kerberos and configure the parameter Define host name-to-Kerberos realm mapping
- Create a new entry with the following values:
- Value name: KERBEROS.MICROSOFTONLINE.COM
- Value: <AppFQDN1>;<AppFQDN2>
(ex: intranet.maximerastello.com;mail.maximerastello.online)
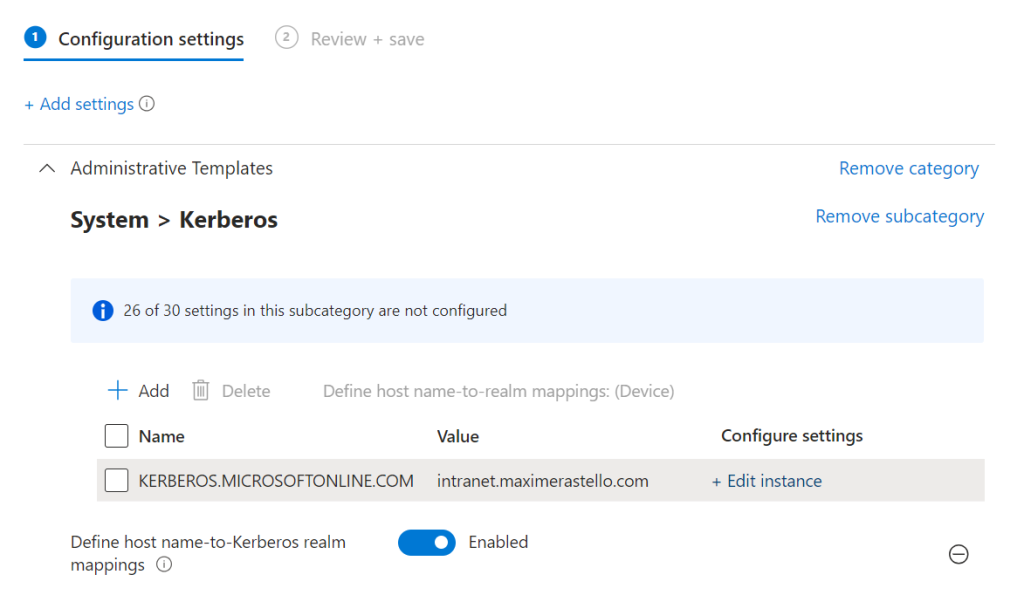
Using Microsoft Intune
- Create a new Windows configuration profile using Settings Catalog
- Go to Administrative Templates > System > Kerberos and add the setting Define host name-to-Kerberos realm mapping
- Set the following parameters:
- Name: KERBEROS.MICROSOFTONLINE.COM
- Value: <AppFQDN1>;<AppFQDN2>
(ex: intranet.maximerastello.com;mail.maximerastello.online)
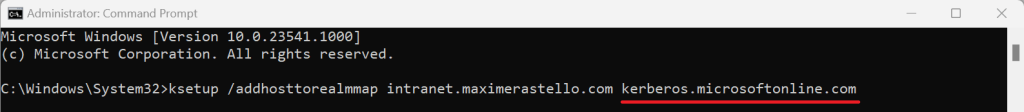
Using Command Line
- Open a Command Prompt or a PowerShell console as an administrator
- Enter the following command:ksetup /addhosttorealmmap <AppFQDN> KERBEROS.MICROSOFTONLINE.COM
This will create a new registry key in HKLM\SYSTEM\CurrentControlSet\Control\Lsa\Kerberos\HostToRealm